Menu




SOC 2 is a vital auditing process ensuring that your service providers handle your data securely, safeguarding both your organization’s interests and the privacy of its clients. For security-minded businesses, SOC 2 compliance is a foundational requirement when selecting a SaaS provider.
This comprehensive framework defines criteria across five trust service principles:
Moreover, SOC 2 is not just a checkbox exercise; it’s a critical audit procedure that verifies a company’s organizational security controls and practices. It’s often the initial compliance standard chosen by SaaS companies, establishing trust with customers and becoming the go-to benchmark for assessing the security of their SaaS suppliers.
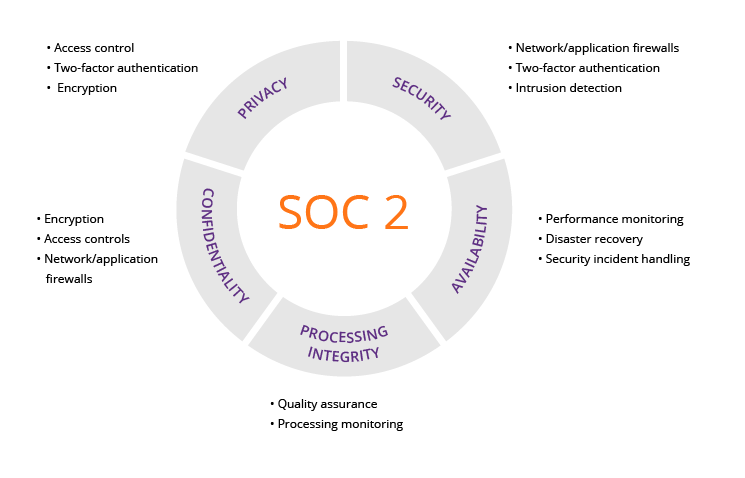
There are two different types of SOC 2 reports you pursue: a SOC 2 Type 1 and a SOC 2 Type 2.
A SOC 2 Type 1 reflects the cybersecurity program as it was on the day it was completed. A SOC 2 Type 2 evaluates a company’s security over a period of time, usually 3 to 12 months. A company must demonstrate to the auditor that it is adhering to its security program over the entire time period.
Most enterprise clients will not buy your product if you don’t meet a number of security requirements.
SOC 2 helps you do precisely that – show your clients and prospective customers that you have put in place the right security measures to protect their data.
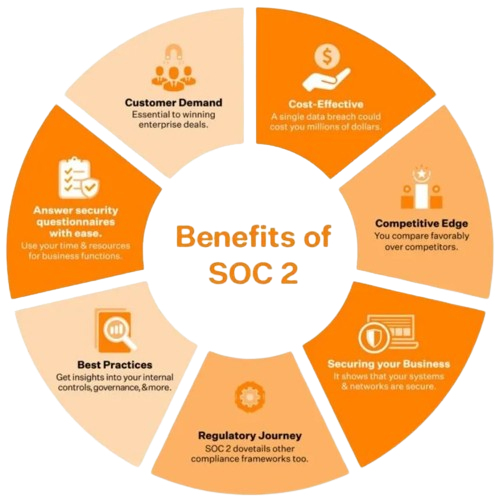
Enhanced Security: Demonstrate your commitment to protecting sensitive data, instilling trust in both current and prospective clients.
Competitive Advantage: Stand out in the market by showcasing your adherence to stringent security standards, setting yourself apart from competitors.
Attract Enterprise Clients: Meet the rigorous security requirements of enterprise clients, positioning yourself as a preferred partner for their business needs.
Industry Recognition: Gain recognition as a trusted leader in your field, bolstering your reputation and credibility within the industry.
Mitigated Risks: Reduce the risk of data breaches and compliance violations, safeguarding your business interests and ensuring continuity.
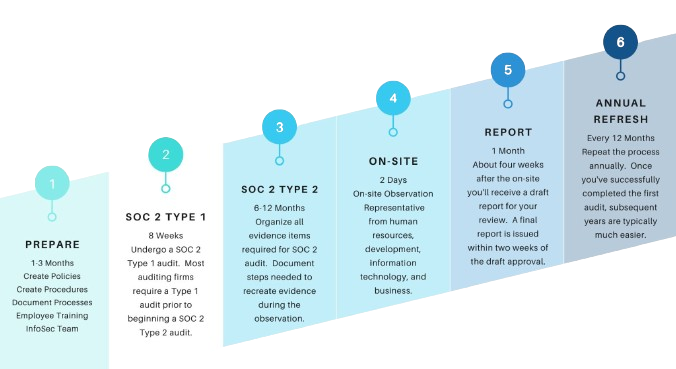
Here’s how we streamline the SOC 2 compliance process at Soter Advisory, ensuring efficiency and peace of mind for your business.
Streamlined Compliance Automation: Accelerate your SOC 2 compliance journey with Soter Advisory’s cutting-edge compliance automation platforms, reducing time and effort for SOC 2 compliance significantly. We partner with the best providers on the market today.
Tailored Technology Solutions: Soter Advisory implements advanced technologies and controls aligned with each SOC 2 criterion, simplifying audits for your business.
Expert Auditor Partnerships: Collaborate with trusted auditors specialized in SOC 2 compliance, ensuring comprehensive assessments and reliable outcomes.
Comprehensive Criteria Audit: